Understanding bash vs dash — What Every DevOps Engineer Should Know

When writing shell scripts or running automation tools like Ansible, you’ll often see /bin/sh, /bin/bash, or even errors like: This confusion stems from differences between bash and dash — two popular Unix shells. Let’s explore what they are, how they differ, and when it matters. What is bash ? Bash stands for Bourne Again Shell. It’s: Key Features of Bash: What is dash ? dash stands for Debian Almquist Shell. It’s: What dash lacks: bash vs dash: A Side-by-Side Feature bash dash POSIX compliant Mostly Fully Arrays Yes No [[ … ]] Yes No set -o pipefail Yes No Brace expansion ( {1..5} ) Yes No Speed Slower Faster Installed by default Most distros Debian/Ubuntu Example That Works in Bash but Fails in Dash This will fail in dash (/bin/sh on Ubuntu) with: It works fine in bash. Why This Matters in DevOps & Ansible ? In tools like Ansible, the shell module runs commands via /bin/sh by default. On Ubuntu/Debian systems, /bin/sh → dash, which means: How to Switch /bin/sh to Bash (if needed) This will update /bin/sh → /bin/bash. Best Practices #ansible #skillupwithsachin #blogs #bash #dash Youtube: https://www.youtube.com/@skillupwithsachin
Breaking Down Kubernetes Interviews – One Pod at a Time!

Introduction: Why Container Orchestration? Problem Statement:As microservices-based applications scale, managing containers across multiple environments manually becomes inefficient and error-prone. Solution:Container orchestration automates the deployment, scaling, networking, and lifecycle management of containers. Key Benefits of Kubernetes Orchestration: Virtual Machines vs Containers vs Kubernetes Virtual Machines Docker Containers Kubernetes Hardware-level virtualization OS-level virtualization Container orchestration Heavyweight Lightweight and fast Automates container ops Boot time: Minutes Boot time: Seconds Self-healing, scalable Key Insight:Containers solve the portability problem. Kubernetes solves the scalability and reliability problem of containers in production. Storage in Kubernetes (Dynamic & CSI) Problem Statement:How do we abstract and dynamically provision storage in Kubernetes without being tied to a specific cloud or on-premise provider? Solution: Flow:App → PVC → StorageClass + CSI → PV Reference: https://kubernetes.io/blog/2019/01/15/container-storage-interface-ga/ Kubernetes Architecture Control Plane (Master Node): Together, these components form the master control plane, which acts as the brain and command center of the Kubernetes cluster. Worker Node (Data Plane): Worker nodes, also known as worker machines or worker servers, are the heart of a Kubernetes cluster. They are responsible for running containers and executing the actual workloads of your applications. Architecture Flow Example: Triggers → API Server → Scheduler → Etcd → Node → Kubelet → Container Runtime Instruction Flow (From YAML to Running Pod) PODS Pods are fundamental building blocks in Kubernetes that group one or more containers together and provide a shared environment for them to run within the same network and storage context. Allows you to colocate containers that need to work closely together within the same network namespace. They can communicate using localhost and share the same IP address and port space. Containers within a Pod share the same storage volumes, which allows them to easily exchange data and files. Volumes are attached to the Pod and can be used by any of the containers within it. Kubernetes schedules Pods as the smallest deployable unit. If you want to scale or manage your application, you work with Pod replicas, not individual containers. A Pod can include init containers, which are containers that run before the main application containers. Kubernetes High Availability & Failure Scenarios Component Failure Impact Recovery API Server Cluster becomes unmanageable Restart or HA deployment Etcd State loss, no new scheduling Restore from backup, use HA etcd Scheduler No new pods scheduled Restart scheduler Controller Manager Auto-scaling and replication broken Restart or recover HA Kubelet Node disconnected, unmonitored pods Restart kubelet or reboot node Kube-Proxy Service communication broken Restart kube-proxy CoreDNS DNS lookup failure for services Restart CoreDNS Reference: https://kubernetes.io/docs/setup/production-environment/tools/kubeadm/high-availability/ Kubernetes Services In Kubernetes, Services are a fundamental concept that enables communication and load balancing between different sets of Pods, making your applications easily discover able and resilient. Why Do We Need Kubernetes Services? Types of Services: Cluster IP: The default service type. It provides internal access within the cluster. NodePort: Opens a port (30000–32767) on each node, allowing external access to services. Make sure to configure security groups accordingly. LoadBalancer: Distributes incoming traffic across multiple pods, ensuring high availability and better performance. Ingress: HTTP routing with host/path rules Network Policies (Ingress & Egress) Problem Statement:How do we secure communication between microservices in a Kubernetes cluster? Use Case: 3-Tier Microservice Architecture Ingress Policy: Egress Policy: Secrets & ConfigMaps Resource Purpose Security Level Config Map Store non-sensitive config Plain text in etcd Secret Store Sensitive Data Base-64 encoded, more secure Practical Use Case: Kubernetes CI/CD Integration (Brief Outline) Problem Statement: How do we automate builds, tests, and deployments on Kubernetes? Approach: How to handle CrashLoopBackOff Error ? Error Message: kubectl get podsNAME READY STATUS RESTARTS AGEmy-app-5c78f8d6f5-xyz12 0/1 CrashLoopBackOff 5 3m Cause: Application inside the container is crashing repeatedly.Missing dependencies, incorrect configuration, or resource limitations.Fix: Check logs for error messages: kubectl logs my-app-5c78f8d6f5-xyz12 Describe the pod for more details: kubectl describe pod my-app-5c78f8d6f5-xyz12 Fix application errors or adjust resource limits. How to fix ImagePullBackOff Error ? Error Message: kubectl get podsNAME READY STATUS RESTARTS AGEmy-app-5c78f8d6f5-xyz12 0/1 ImagePullBackOff 0 3m Cause: Fix: kubectl describe pod my-app-5c78f8d6f5-xyz12 containers: – name: my-app image: myregistry.com/my-app:latest kubectl create secret docker-registry regcred \ –docker-server=myregistry.com \ –docker-username=myuser \ –docker-password=mypassword How to fix Pod Stuck in “Pending” State ? Error Message: kubectl get podsNAME READY STATUS RESTARTS AGEmy-app-5c78f8d6f5-xyz12 0/1 Pending 0 5m Cause: Fix: kubectl describe pod my-app-5c78f8d6f5-xyz12 kubectl get nodes kubectl get pvc How to fix Node Not Ready ? Error Message: kubectl get nodesNAME STATUS ROLES AGE VERSIONnode-1 NotReady <none> 50m v1.27.2 Cause: Fix: kubectl describe node node-1 journalctl -u kubelet -n 100 systemctl restart kubelet df -h How to fix Service Not Accessible error? Error Message: curl: (7) Failed to connect to my-service port 80: Connection refused Cause: Fix: kubectl get svc my-service kubectl describe svc my-servic kubectl get pods -o wide How to fix “OOMKilled” (Out of Memory) ? Error Message: kubectl get pod my-app-xyz12 -o jsonpath='{.status.containerStatuses[0].state.terminated.reason}’OOMKilled Cause: Fix: resources: limits: memory: “512Mi” requests: memory: “256Mi” kubectl top pod my-app-xyz12 What do you know about kubeconfig file in Kubernetes ? A file used to configure access to a cluster is called a kubeconfig file. This is the generic way of referring to a configuration file. This doesn’t mean the file name is kubeconfig. K8s components like kubectl, kubelet, or kube-controller-manager use the kubeconfig file to interact with the K8s API. The default location of the kubeconfig file is ~/.kube/config. There are other ways to specify the kubeconfig location, such as the KUBECONFIG environment variable or the kubectl —kubeconfig parameter. The kubeconfig file a YAML file contains groups of clusters, users, and contexts. The clusters section lists all clusters that you already connected. The users section lists all users already used to connect to a cluster. There are some possible keys for the user: The context section links a user and a cluster and can set a default namespace. The context name is arbitrary, but the user and cluster must be predefined in the kubeconfig file. If the namespace doesn’t exist, commands will fail with an error. What are Selectors & Labels in Kubernetes? Services use selectors and labels to identify the Pods they should target.
Understanding printf in Scripting: Usage, Examples, and Alternatives

When it comes to printing output in programming, printf is one of the most commonly used functions, especially in languages like C, Shell scripting, and Java. Understanding its functionality, capabilities, and alternatives can significantly enhance your coding experience. What is printf? The printf function stands for “print formatted” and is used to print formatted output to the console. It provides a powerful way to display text, numbers, and other data types in a customized format. Primarily, it is a standard library function in C but is also available in shell scripting for Unix/Linux environments. Syntax in Shell Scripts: Unlike echo, which simply prints text, printf provides advanced formatting capabilities. Common Usage and Examples in Shell Scripts Basic Printing The simplest use of printf is to display static text: Note: Unlike echo, you must explicitly include \n for a new line. Printing Variables You can use format specifiers to print variable values: Formatting Numbers printf allows precise control over numerical output: Creating Aligned Tables You can use width specifiers to align output: Output: Using %q in Shell printf The %q specifier in printf escapes special characters in a string, making it useful for safe and predictable output, especially when dealing with untrusted input or special characters. Example: Output: This is particularly helpful in scripts where inputs might include spaces, quotes, or other characters requiring escaping. Combining %q with Other Specifiers: Output: Format Specifiers in Shell printf Here are some common placeholders used in shell scripting with printf: Differences Between printf and echo Alternatives to printf in Shell Scripts While printf is versatile, there are alternatives for simpler tasks: 1. “ The echo command is simpler and often sufficient for basic output. 2. “** for Advanced Formatting** awk can be used for complex text processing and formatting. 3. “** for Static Text** For displaying static text files or strings, cat is an option: When to Use printf in Shell Scripts Scenario-Based Interview Questions and Answers 1. How would you use “ to escape special characters in a user input string? Answer: Use the %q format specifier to ensure that special characters are escaped. This will output: Hello,\ \$USER! 2. How can you format a floating-point number to show exactly three decimal places? Answer: Use %.3f in the format specifier. This will output: 3.142 3. How can you create a table with aligned columns using “? Answer: Use width specifiers to align the text. 4. What happens if a format specifier does not match the argument type? Answer: The output may be unpredictable, as printf does not perform type checking. For example: This could cause an error or display an unintended result. 5. How do you print a literal ** character using **? Answer: Use %% in the format string. This will output: Progress: 50% The printf command is a powerful tool in shell scripting, offering advanced formatting capabilities beyond what echo can provide. Its versatility makes it a go-to choice for scripts that require precision and control over the output format. While simpler alternatives exist, understanding and leveraging printf ensures your shell scripts are robust and professional. Experiment with printf in your shell scripts and discover how it can streamline and enhance your output!
AWS EC2 Status Checks: An Overview
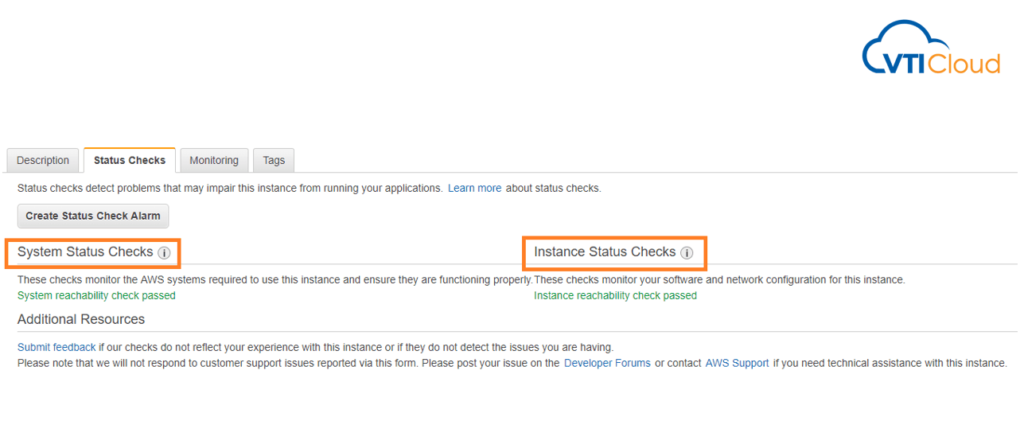
AWS EC2 status checks are automated health checks that monitor the functionality and operability of your EC2 instances. They provide crucial insights into the state of the underlying hardware, network connectivity, and the operating system of the instance. These checks are fundamental to ensure the high availability and reliability of your workloads on AWS. Types of EC2 Status Checks Default Configuration of Status Checks By default, status checks are enabled for every EC2 instance upon launch. These checks are configured and managed by AWS automatically. The results of these checks are visible in the AWS Management Console under the “Status Checks” tab of an EC2 instance, or via the AWS CLI and SDKs. Can We Modify Default Configuration? AWS does not provide options to directly alter the predefined system and instance status checks. However, you can customize the handling of failed checks by configuring CloudWatch Alarms: Defining Custom Health Checks While AWS EC2 status checks focus on the infrastructure and OS-level health, you might need additional monitoring tailored to your application or workload. This is where custom health checks come in. Here’s how to implement custom checks: sudo yum install amazon-cloudwatch-agentsudo vi /opt/aws/amazon-cloudwatch-agent/etc/amazon-cloudwatch-agent.json Example configuration snippet: { “metrics”: { “append_dimensions”: { “InstanceId”: “${aws:InstanceId}” }, “metrics_collected”: { “disk”: { “measurement”: [“used_percent”], “resources”: [“/”] }, “mem”: { “measurement”: [“used_percent”] } } }} Start the cloudwatch agent:sudo /opt/aws/amazon-cloudwatch-agent/bin/amazon-cloudwatch-agent-ctl -a start Example: Status Check Handling Scenario: Automate recovery when a system status check fails. { “Version”: “2012-10-17”, “Statement”: [ { “Effect”: “Allow”, “Action”: [“ec2:RebootInstances”], “Resource”: “*” } ]} 2. Create a CloudWatch alarm: 3. Test: Interview Questions and Answers
Managing Containers Without Kubernetes: A Glimpse Into Challenges and Solutions
Imagine a world without Kubernetes. A world where containers, those lightweight, portable units of software, existed, but their management was a daunting task. Let’s delve into the challenges that developers and operations teams faced before the advent of this powerful tool. A World Without Kubernetes Before Kubernetes, managing containers was a complex and error-prone process. Here are some of the key challenges: Alternatives Without Kubernetes A Real-World Scenario: A Microservices Architecture Consider a typical microservices architecture, where a complex application is broken down into smaller, independent services. Each service is deployed in its own container, offering flexibility and scalability. Without Kubernetes: Kubernetes to the Rescue Kubernetes revolutionized container orchestration by automating many of these tasks. It provides a robust platform for deploying, managing, and scaling containerized applications. The Challenges of Managing Containers Without Kubernetes The absence of Kubernetes would force us to rely on fragmented tools and custom solutions, each addressing a piece of the orchestration puzzle. The challenges of scaling, monitoring, and ensuring reliability would increase operational complexity, delay deployments, and impact developer productivity. Thankfully, Kubernetes exists, empowering us to focus on building applications rather than worrying about infrastructure.
The Dual Edges of Adaptive AI: Navigating Hidden Risks in the Age of Smart Machines
IntroductionAdaptive AI holds tremendous promise—its ability to learn, adjust, and evolve as it encounters new data or scenarios is a leap toward intelligent, responsive technology. However, this continual evolution also brings unique and often hidden risks. As Adaptive AI grows more deeply embedded in our lives and decision-making, we need to understand the shadows it casts, the risks lurking in its complexity, and the implications for data privacy, security, and fairness. 1. Data Leaks: The Cracks in the Pipeline Imagine your personal information as water in a tightly sealed pipe. When a data leak occurs, it’s like a crack in that pipe, allowing private information to escape without your knowledge. In the world of Adaptive AI, where vast amounts of data flow into models to improve learning and accuracy, these leaks can be devastating, potentially exposing passwords, credit card numbers, and other sensitive data to unintended parties. 2. Data Poisoning: Contaminating the Learning Pool Picture a serene lake from which an AI learns, gathering information and forming decisions based on what it finds in the water. Data poisoning is the equivalent of someone secretly dumping toxic waste into that lake. When Adaptive AI trains on contaminated or intentionally misleading data, it results in incorrect conclusions or harmful behaviors, just as drinking poisoned water could make one sick. This malicious tampering can skew outcomes, leading to decisions that may harm individuals, businesses, or entire systems. 3. Training Data Manipulation: Misinforming the Mind Consider a textbook deliberately altered by a teacher, giving incorrect answers to certain questions. When an AI model learns from manipulated data, it forms inaccurate associations or biases, which can lead to unfair or flawed outcomes. In the hands of Adaptive AI, which continuously evolves with new data, this misinformation becomes more potent and potentially more harmful, impacting areas like hiring, lending, and even criminal justice. 4. Model Inversion: Peeking Inside the Locked Box Adaptive AI models can be thought of as locked boxes that take in questions and provide answers, without revealing their internal workings. Model inversion, however, is akin to a burglar discovering how to unlock that box, reconstructing the sensitive data that was used for training. This exposure could compromise private information, especially if sensitive health, financial, or personal data was involved, posing significant privacy risks. ConclusionThe evolving intelligence of Adaptive AI brings as much risk as it does reward. As it advances, we must remain vigilant and proactive in addressing the hidden dangers, from data leaks and poisoning to manipulation and inversion risks. Safeguarding against these threats is essential to ensure Adaptive AI not only grows smarter but also operates responsibly, securely, and fairly in our digital future.
The Three Dilemmas : Choice, Control & Intelligence – DevOps Leaders Face When Scaling Continuous Delivery Pipelines
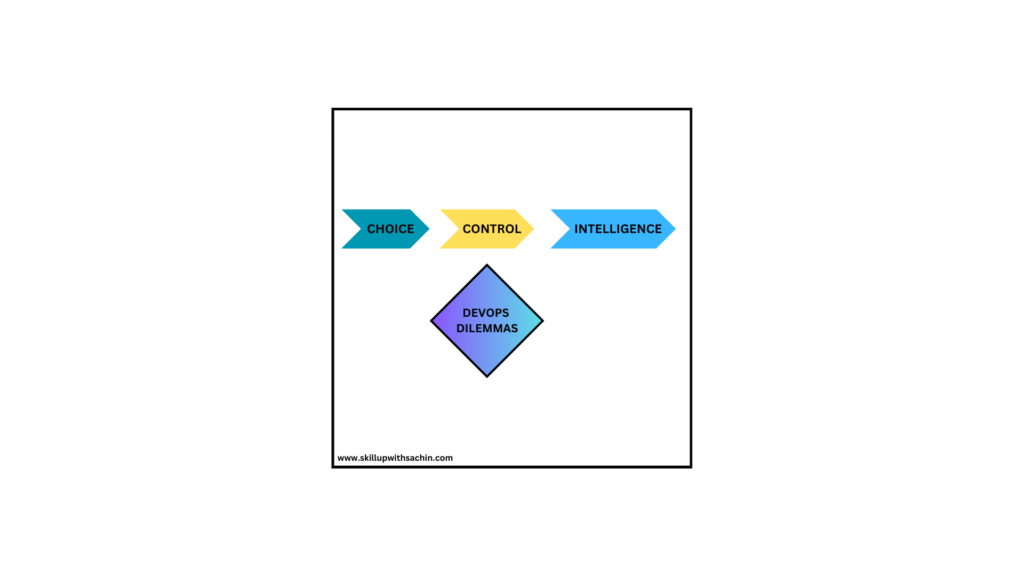
In the age of digital transformation, scaling continuous delivery (CD) pipelines has become essential for businesses striving for agility and competitiveness. However, DevOps managers often find themselves in a balancing act, facing multiple dilemmas that can impact the efficiency of their pipelines. These dilemmas can be broadly categorized into Choice, Control, and Intelligence. Understanding and addressing these challenges is critical for fostering sustainable growth and delivering high-quality software at scale. 1. The Dilemma of Choice: Choosing the Right Tools and Technology Stack One of the first dilemmas DevOps leaders face is making the right choices about the tools and technologies that will power their continuous delivery pipeline. The market is saturated with options for CI/CD platforms, containerization, orchestration tools, and cloud services. While choice offers flexibility, it also creates complexity. Picking the wrong tool could lead to vendor lock-in, scalability bottlenecks, or inefficient processes. For example, a DevOps manager may need to choose between open-source CI/CD tools like Jenkins, which provides flexibility but requires heavy customization, or managed services like GitLab CI or CircleCI, which offer ease of use but may not be as customizable. Another growing trend is the adoption of GitOps for declarative infrastructure management, but organizations often struggle to determine if it suits their unique scaling needs. Solution:To overcome the choice dilemma, leaders should: 2. The Dilemma of Control: Balancing Standardization and Autonomy The second dilemma arises around control—balancing the need for standardization with the autonomy required by individual teams. As the organization grows, it’s tempting to standardize tools, processes, and environments to ensure consistency and reduce risk. However, excessive control can stifle innovation and agility, especially when diverse teams have differing needs. Consider a scenario where a DevOps team has standardized its pipeline on a certain cloud provider’s services for deployment. However, a new development team, working on an experimental project, wants to leverage a different technology stack, such as Kubernetes on-premises or a multi-cloud strategy. Imposing strict control over tool choices can lead to friction between innovation and governance. Solution:To address the control dilemma: 3. The Dilemma of Intelligence: Leveraging Data for Decision-Making The third dilemma is intelligence—leveraging data effectively to make informed decisions about the performance and reliability of the CD pipeline. With pipelines spanning multiple tools and environments, gathering actionable insights across the stack can be challenging. Leaders must decide which metrics matter most, such as deployment frequency, lead time, and failure rates, while avoiding the trap of analysis paralysis. For example, a team may gather vast amounts of data from their CI/CD pipeline (build times, test results, deployment success rates) but struggle to correlate this data to business outcomes. Should the focus be on speeding up deployments, or is it more critical to reduce failure rates? Without the right intelligence, it becomes difficult to prioritize improvements. Solution:To handle the intelligence dilemma: Conclusion Scaling continuous delivery pipelines is no easy feat, and DevOps leaders must navigate the dilemmas of choice, control, and intelligence. By carefully selecting tools that align with long-term goals, striking a balance between standardization and team autonomy, and utilizing data to drive decision-making, organizations can successfully scale their pipelines while maintaining agility and quality. Addressing these dilemmas head-on not only improves the scalability and efficiency of CD pipelines but also fosters a culture of innovation, where teams can continuously deliver value to end users.
The Shift-Left Strategy: Catching Security Issues Early
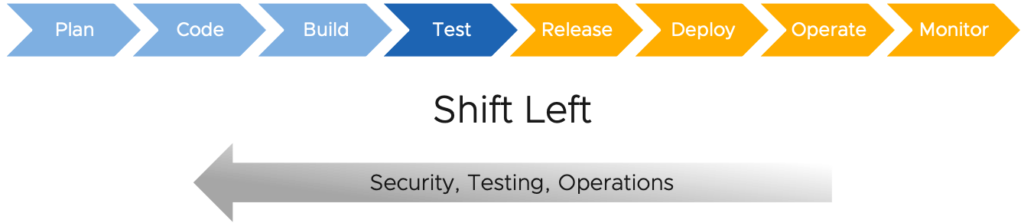
In the fast-paced world of software development, finding and fixing security vulnerabilities as early as possible is crucial. That’s where the Shift-Left Strategy comes into play. It’s all about moving security testing and code reviews to the beginning of the development process—before the code even gets close to production. By shifting security left in your DevOps pipeline, you catch issues early, reduce risks, and save time in the long run. Here are some simple tips to help you adopt this strategy !! 1. Start with Secure Code Reviews Before any code is merged into your project, it should go through a security review. This helps to spot vulnerabilities like insecure coding practices or risky dependencies from the get-go. Tip:Integrate security reviews as part of your regular code reviews. Tools like SonarQube or Codacy can help you automate code analysis and catch security flaws early. 2. Include Security in CI/CD Pipelines Your Continuous Integration (CI) and Continuous Delivery (CD) pipelines are ideal places to implement automated security checks. This way, every time new code is committed, it gets tested for security issues. Tip:Use tools like Snyk, Checkmarx, or Aqua Security to scan for vulnerabilities in your code, dependencies, and container images during each build and deployment. 3. Shift Security Testing Left Security testing often happens after development is done, but with the Shift-Left approach, it happens much earlier. By incorporating security tests into unit and integration tests, teams can find vulnerabilities during the development process itself. Tip:Set up static and dynamic security tests as part of your testing suite. Static Application Security Testing (SAST) tools can analyze your code for flaws, while Dynamic Application Security Testing (DAST) tools simulate attacks on running applications. 4. Collaborate Early and Often Security isn’t just the responsibility of the security team—it’s everyone’s job. Developers, testers, and security teams should collaborate right from the design phase to ensure security is baked into every step of the project. Tip:Encourage cross-team collaboration with regular meetings and shared security practices. This will help bridge gaps and ensure security is part of the entire development lifecycle. 5. Automate Security Policies To catch security issues early and consistently, use automated tools to enforce security policies. This ensures that any code that doesn’t meet security standards is flagged immediately, long before it can cause problems in production. Tip:Integrate security policies using tools like Open Policy Agent (OPA) or Kubernetes Admission Controllers to enforce compliance across your pipelines and infrastructure. 6. Educate Your Team Adopting a Shift-Left strategy means that everyone on the development team needs to be security-conscious. Training developers on common security threats, vulnerabilities, and best practices can go a long way in preventing security issues. Tip:Provide regular training on secure coding practices and how to use security testing tools effectively. This empowers developers to think about security as they code. Conclusion The Shift-Left Strategy empowers teams to address security issues before they become costly problems. By integrating security checks, tests, and reviews early in the DevOps process, organizations can build more secure applications from the start, reduce risks, and save time.
Choosing the Right Gateway: Navigating API Gateway vs Ingress Controller vs NGINX in Kubernetes
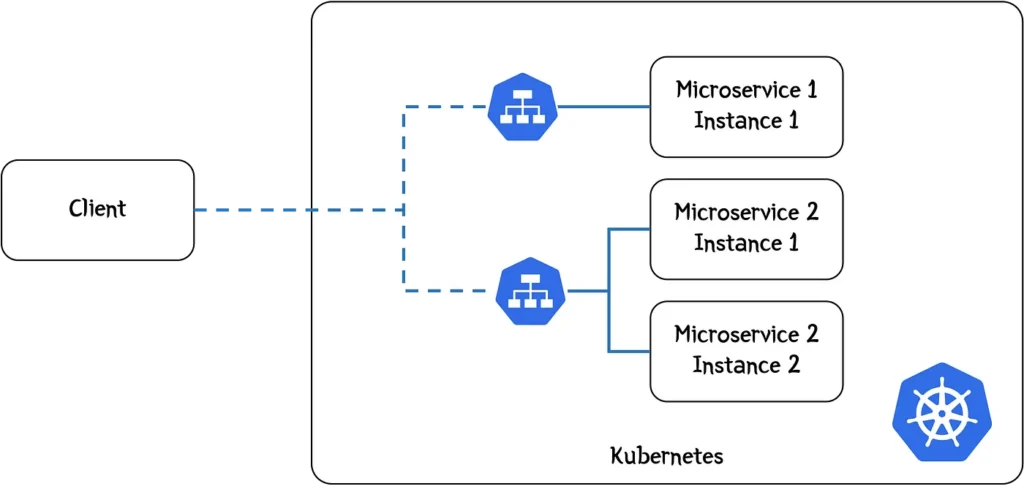
When building microservices-based applications, it can be challenging to determine which technology—API Gateway, NGINX, or an Ingress Controller—is best for connecting services. These tools play distinct roles in managing traffic, but each has its own set of strengths depending on the use case. Understanding the Key Components: Choosing the Right Solution: Real-World Use Cases: #Pseudo Code for API Gateway routingroutes: – path: /order-history services: – user-service – order-service 2. Internal Application in KubernetesFor a simple internal application where different teams use distinct services, an Ingress Controller can be set up to manage HTTP/S routing, exposing internal applications securely within the cluster. # Pseudo Ingress RuleapiVersion: networking.k8s.io/v1kind: Ingressmetadata: name: internal-appspec: rules: – host: app.internal.example.com http: paths: – path: /team1 backend: service: name: team1-service port: number: 80 3. Hybrid SolutionA hybrid scenario might use both an API Gateway for external API requests and NGINX as a load balancer within the Kubernetes cluster. This setup is common for public-facing applications where internal service-to-service communication requires more granular control. Choosing between an API Gateway, Ingress Controller, or NGINX boils down to your application needs. API Gateways are best for complex routing and security, while Ingress Controllers are ideal for HTTP routing in Kubernetes, and NGINX offers flexibility for custom traffic management. Advanced Use Case: Advanced Use Case: Microservices-based Financial Platform with API Gateway, NGINX, and Service Mesh Imagine a financial platform where you handle multiple services like user authentication, payments, and transactions. In this scenario: Architecture: Pseudocode Example: This setup can include defining an API Gateway for external APIs, and using an Ingress Controller for internal routing. For inter-service communication, a Service Mesh will enforce security and provide monitoring. Code Link: https://github.com/sacdev214/apigatwaycode.git This architecture ensures that: Scenario-Based Questions and Answers: 1. Scenario: You are working with a simple Kubernetes cluster running internal services with no external traffic. Which component would be best to route traffic between these services? 2. Scenario: A public-facing e-commerce website needs to handle thousands of requests per minute, with several microservices handling user profiles, orders, and payments. Which component should you use for managing these requests efficiently? 3. Scenario: You need to enforce strict rate limiting, traffic throttling, and security policies on external APIs exposed by your Kubernetes services. Which tool should you consider? 4. Scenario: Your application is deployed on Kubernetes and has simple HTTP services that need exposure to the internet. What is the most Kubernetes-native solution? 5. Scenario: You are building a microservices architecture where each service communicates with others via HTTP, and you need to ensure inter-service communication is secure and well-monitored. Which solution would be best?
Observability in Linux Performance: A Visual Guide
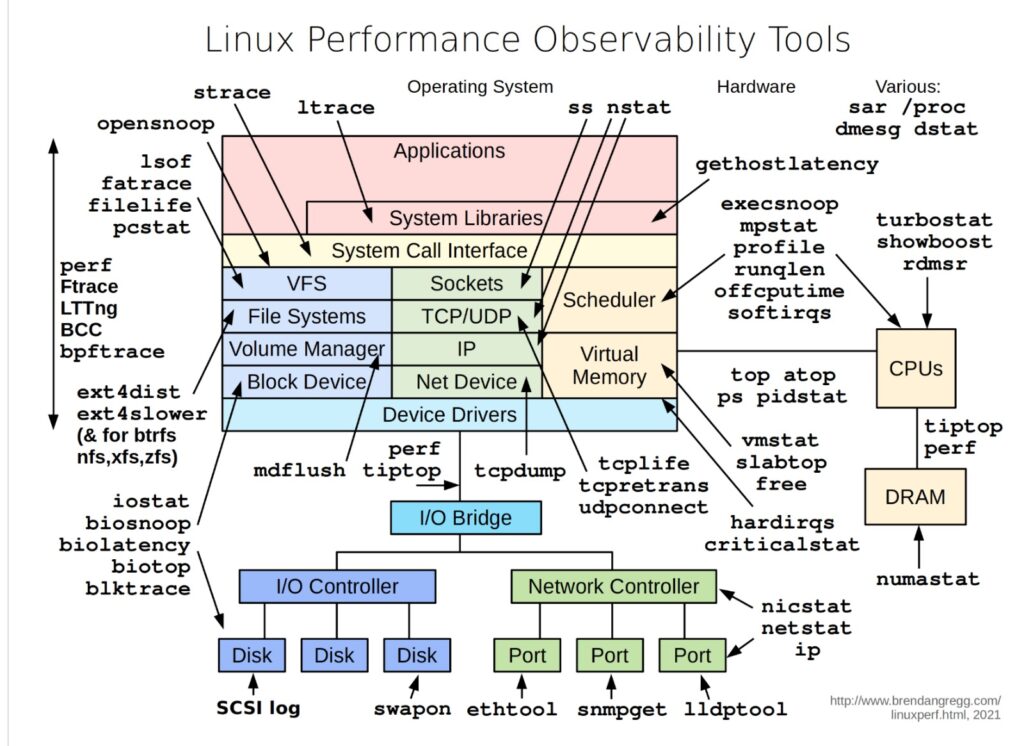
In today’s world, where the performance of systems is critical to business success, understanding and monitoring Linux performance is more important than ever. The visual guide provided above is a powerful tool for system administrators, DevOps engineers, and SREs to gain insights into the various components of a Linux system, from hardware to applications, and how they interact. Understanding the Layers of Linux Performance The diagram breaks down Linux performance observability into multiple layers, each representing different parts of the system: Example Use Cases Conclusion This visual guide is not just a map but a toolkit that offers a structured way to approach Linux performance issues. Each tool has its place, and by understanding where and how to use them, you can effectively diagnose and resolve performance bottlenecks, ensuring your systems run smoothly and efficiently. For anyone serious about maintaining high-performance Linux environments, mastering these tools and understanding their use cases is not optional — it’s essential.


